30 min
Fablabs Course
3.3.1.1 Session: Introduction to digital accounts and funds
Accounts authentication (10 min)
Empathize phase
- present the students with the scenario
- Bob wants to transfer some money to Alice using an online banking system.
- Bob needs to ensure that the person he is sending money to is indeed Alice, not someone pretending to be her (EVE).
- Similarly, Alice needs to ensure that any notifications or messages she receives regarding the money transfer come from Bob, not someone else trying to deceive her.
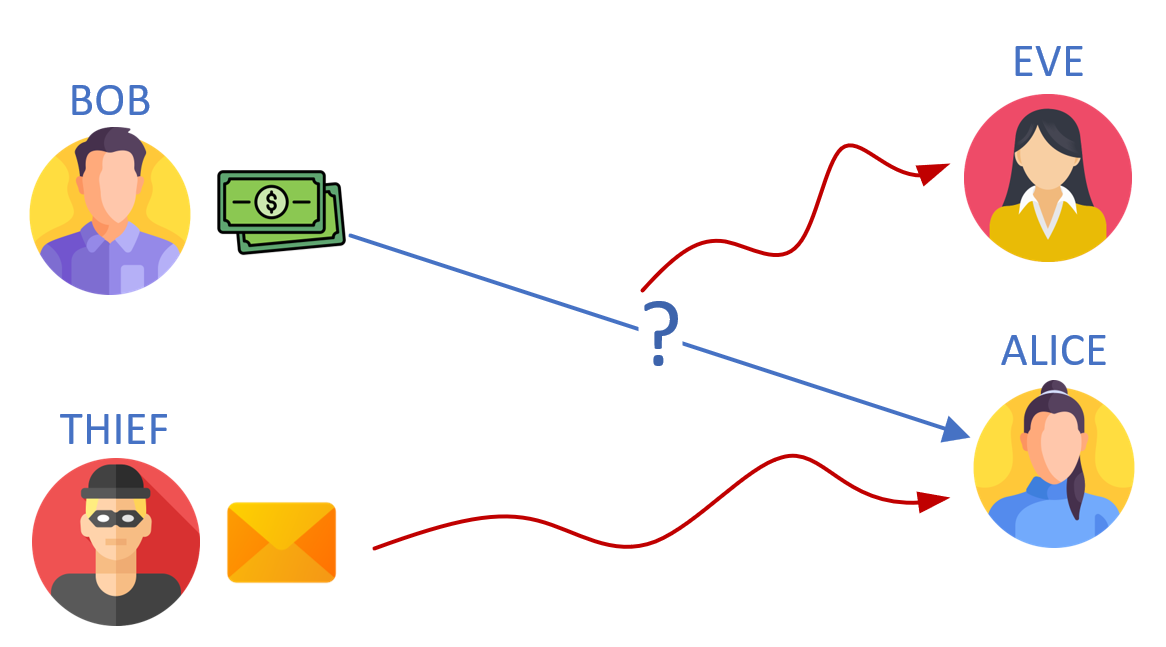
- Discuss what damage Eve and the thief can inflict on Bob and Alice (message interception, manipulation, ….)
Define phase
- Students need to clearly articulate the problem of authentication within the context of digital security. They need to identify the key elements that need to be addressed to ensure that users can verify their identity securely and that communications or transactions are conducted with verified parties only.
- Students should consider different methods of verifying identity, such as passwords, biometrics, or cryptographic keys.
- Discuss the pros and cons of each method
Accounts authorisation (10 min)
Empathize phase
- Present students with a scenario
- Bob has successfully authenticated himself and now wants to transfer $1,000 to Alice using the online banking system. However, Bob's account has different levels of permissions.
- Bob’s account allows him to view balances and transfer up to $500 without additional approval. For amounts over $500, Bob must have authorization from his manager, Charlie.
- Alice receives a notification that money has been transferred to her account. However, Alice’s account has a restriction where she can only withdraw amounts less than $200 without additional verification.
- Eve, who is trying to exploit the system, might try to transfer more money than Bob is authorized to or withdraw more from Alice's account than she is allowed to.
- Discuss the potential consequences if authorization is not properly managed:
- What could happen if Bob could transfer amounts beyond his authorization?
- What if Alice could withdraw more than her account is authorized to handle?
- How could Eve exploit these weaknesses if authorization controls are not in place?
Define phase
- Students need to discuss and define different types of authorization:
- Role-Based Access Control (RBAC): Determine the roles of users like Bob, Charlie, and Alice, and what actions each role is permitted to perform.
- Attribute-Based Access Control (ABAC): Discuss the possibility of using attributes like transaction amount or time of day to further refine permissions.
- Access Control Lists (ACLs): Consider how specific permissions might be assigned directly to user accounts.
- What are the pros and cons of each method?
Digital funds (assets) (10 min)
Empathize phase
Bob, Alice, and Charlie each possess different types of digital assets that they want to sell, trade, or use. However, they face a common challenge: how to ensure that these digital assets are recognized as authentic and valuable by others. The key problem lies in how these assets derive their value and how that value is validated or authenticated.
- Bob's Challenge:
- Digital Art Sale: Bob has created a piece of digital art and wants to sell it online. However, he needs to prove to potential buyers that the art is authentic and that he is the original creator. Without proper authentication, anyone could copy the art and claim it as their own, making it difficult for Bob to establish the value of his work.
- Alice's Challenge:
- Digital Certificate Verification: Alice has earned a digital certificate for completing a professional course. She wants to use this certificate to apply for jobs, but she needs to ensure that employers can verify the certificate’s authenticity. Without a trusted validation method, her certificate might be considered worthless, as anyone could fabricate similar credentials.
- Charlie’s Challenge:
- Blockchain-Validated Asset: Charlie has also earned cryptocurrency through mining on a blockchain network. The cryptocurrency itself is secured and validated by the decentralized consensus of the blockchain. Charlie can use this cryptocurrency to buy digital art, but he must consider whether the seller accepts this form of payment and how its value fluctuates due to market conditions.
- Discussion Points:
- What Makes These Assets Valuable?:
- For Bob’s digital art, the value lies in the authentication provided by the creator (Bob) and his reputation.
- For Alice’s digital certificate, the value is validated by the thirdparty institution, whose reputation and authority lend credibility to the certificate.
- For Charlie’s cryptocurrency, the value is intrinsic to the asset itself, as it is generated through a decentralized, cryptographic process that ensures its uniqueness and scarcity.
- How Do These Sources of Value Differ?:
- User-Authenticated: The value is tied directly to the creator or owner’s reputation and their ability to prove ownership or authorship.
- Third-Party Validated: The value depends on the trust and authority of an external entity that validates the asset.
- Blockchain-Mined: The value is decentralized and inherent to the asset, determined by cryptographic processes and market dynamics rather than any single individual or institution.
- Why Is Authentication Important in These Scenarios?:
- Bob’s Art: Without proper authentication, anyone could claim to have created the art, diminishing its value.
- Alice’s Certificate: Without third-party validation, the certificate would have no recognized value.
- Charlie’s Cryptocurrency: The intrinsic value comes from the network’s ability to authenticate and validate each transaction and asset.
- What Makes These Assets Valuable?:
- Key Takeaways:
- Digital assets can derive their value from different sources, whether it’s the reputation of an individual, the authority of a third party, or the inherent properties of a blockchain system.
- Understanding the source of value is crucial in digital transactions, as it determines how the asset is authenticated, validated, and ultimately, trusted.
Define phase
Students need to define the authentication methods and value propositions for Bob, Alice, and Charlie. They should explore how each option is validated and consider the potential risks and benefits.
- Bob’s Digital Art (Self-Authenticated Asset):
- Authentication: Bob has self-authenticated the digital art using his digital signature. This cryptographic signature proves that Bob is the creator and owner of the artwork.
- Value Source: The value of this asset is tied directly to Bob’s reputation and the uniqueness of his digital signature. The challenge for Charlie is to assess whether Bob’s self-authentication is trustworthy enough to justify the purchase.
- Alice’s Digital Certificate (Third-Party Authenticated Asset):
- Authentication: Alice’s digital certificate is issued and authenticated by a reputable educational authentication service. This third-party validation ensures that the course taken is genuine and the certificate is a reliable proof of authenticity.
- Value Source: The value here is derived from the trust in the third-party service.
- Cryptocurrency (Blockchain-Validated Asset):
- Authentication: The cryptocurrency Charlie owns is validated by the blockchain network, where every transaction is securely recorded and verified by decentralized nodes.
- Value Source: The value of the cryptocurrency comes from the security and decentralized nature of the blockchain. It is not tied to any single entity, but its value can fluctuate based on market demand. Charlie must determine whether the seller accepts this currency and whether he is comfortable with its volatility.
- Key Takeaways:
- Understanding Authentication Methods: Each asset derives its value differently —self-authentication by the creator, third-party validation, and blockchain verification. Students should explore how these methods influence the perceived security and value of the digital asset.
- Evaluating Risk and Trust: We must weigh the trustworthiness of each authentication method against the potential risks. The self-authenticated option depends on Bob’s reputation, the third-party authenticated option relies on an external service’s credibility, and the blockchain option is secure but may be subject to market volatility.
- Decision-Making in Digital Transactions: The scenario highlights the importance of understanding the source of value and authentication in digital transactions, helping students make informed decisions when dealing with various types of digital assets.
Licenciado baixo a Licenza Creative Commons Atribución Compartir igual 4.0